What Are Ransomware Attacks?
Ransomware is a type of malware that encrypts a victim’s files or locks their computer system. The attackers then demand a ransom in exchange for the decryption key or to unlock the system. In 30% of attacks, data was also stolen, enhancing the ransomware attackers’ ability to monetize the attack by threatening to make the stolen data public or sell it.
Ransomware attacks can be harmful to individuals, businesses, and organizations. They can cause financial damage, disrupt operations, and lead to data breaches. Ransomware attacks can also affect sensitive information’s confidentiality, integrity, and availability.
Types of Ransomware Attacks
Ransomware enters a system through malicious email attachments, infected downloads, compromised credentials, or exploiting vulnerabilities in software or networks. Once it infects a system, it encrypts files and file extensions, making them unusable without the decryption key. A ransom note appears on the victim’s screen, providing instructions on paying the ransom and regaining access to the files or system. The note includes a deadline and threats of permanent data loss or increased ransom if the payment is not made within the specified time.
According to Norton Security, these are the most come common types of ransomware:
- Encryption-based ransomware aims to infiltrate and encrypt crucial files on a victim’s computer, such as documents, images, and videos. Cybercriminals withhold access to these files but refrain from disrupting basic computer functions, unlike other ransomware variants. This approach instills a sense of urgency in the user, as they can see their files but are unable to access the content.
- System-locking ransomware is distinct in its objective to lock users out of their own computers. To achieve this, hackers disable essential computer functions while retaining limited mouse and keyboard functionality. This allows the user to comply with the cybercriminal’s demands to regain access to their system.
- Fake alert software, or scareware, is malicious software designed to make false assertions about viruses infecting a user’s computer or device. To resolve these fictitious issues, payment is usually demanded. Some scareware may lock users out of their devices, while others inundate the screen with numerous pop-ups to overwhelm the user.
- Ransomware as a Service (RaaS) is a nefarious business model available on the dark web, designed to simplify ransomware attacks. This software automates all aspects of a ransomware attack for the hacker, from spreading the malware to collecting payments and restoring user access.
- Data exposure malware attack, also known as doxware or leakware, threatens to divulge sensitive data, targeting individuals and businesses alike publicly. When hackers demand payment to prevent the release of confidential information, they capitalize on people’s willingness to do almost anything to prevent their private data from falling into the wrong hands.
Related article: Protection Against Cybercriminal Ransomware During a Pandemic.
Why Ransomware Is a Huge Threat to Businesses
IBM reports that the average ransom payment is over $800,000. In addition to any ransoms paid, organizations reported an estimated average cost to recover from ransomware attacks of $1.82 million, an increase from the 2022 figure of $1.4 million and in line with the $1.85 million reported in 2021. It takes organizations an average of 49 days to identify and fix ransomware breaches, which is longer than other types of attacks.
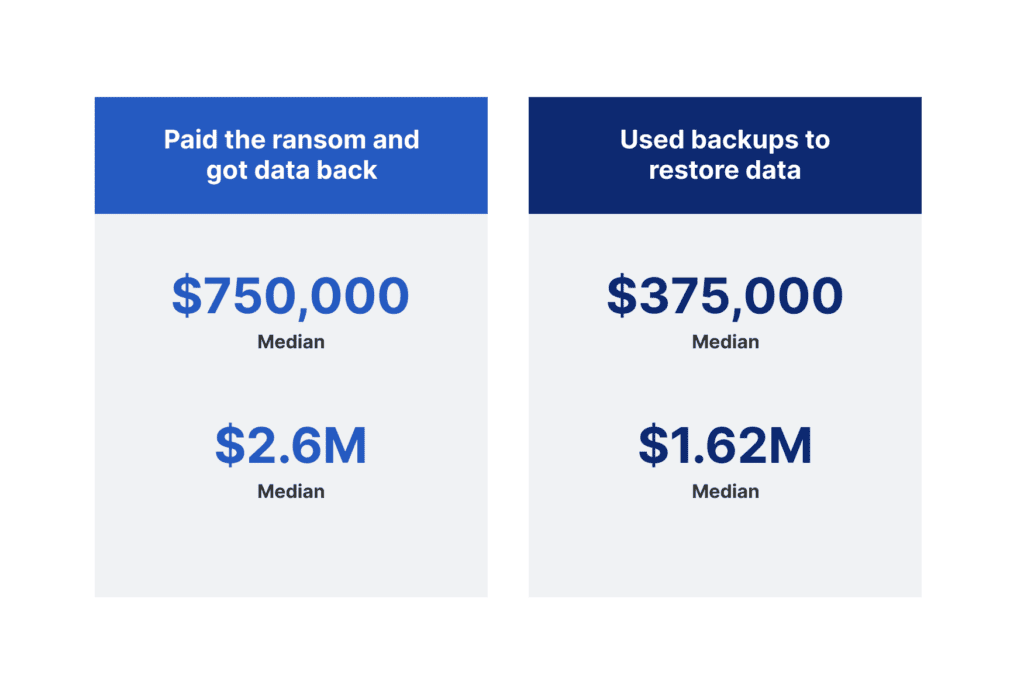
Cost of Ransomware Attack by Data Recovery Method
Analyzing the data shows that relying on backups for recovery from a ransomware attack is significantly more cost-effective than paying the ransom. The median recovery cost for organizations using backups is $375,000, which is half the cost incurred by those who paid the ransom ($750,000). Likewise, the mean recovery cost is nearly $1 million lower for those relying on backups. This evidence reinforces the financial benefits of investing in a robust backup strategy.
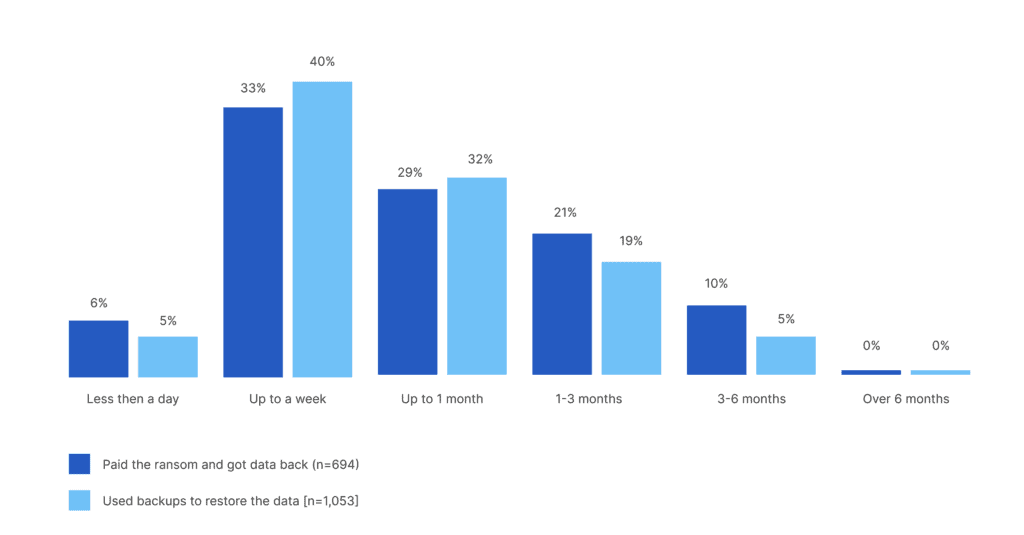
Time Needed to Recover Data Following Ransomware Attack
The study found that organizations using backups to recover their data tend to recover more quickly than those who pay the ransom. Specifically, a week is the average recovery time for companies using backups, whereas 39% of businesses paying the ransom take more than a month to recover. While only 23% (with rounding) of businesses relying on backups experience month-long recoveries, some respondents might have used both methods. Nevertheless, the recovery advantages of backups are evident.
Related article: Increased Risk from Macro-Based Malware.
A recent report on data breaches showed that ransomware attacks surged dramatically in 2022 and were responsible for 25% of all data breaches. Further, according to Sophos, ransomware affected 66% of organizations in 2022, an increase of 78% over 2020. Additionally, it’s expected that these numbers will continue to rise, in part, due to the advent of the “ransomware as a service” (RaaS) industry which now proliferates on the dark web. Just as IT companies have shifted to “as a service” offerings, so has the cybercrime ecosystem.
“Ransomware is a huge threat to companies because it disrupts operations, costs a lot of money, and puts valuable data at risk. It’s crucial for businesses to invest in strong cybersecurity measures, employee training, and regular backups to protect themselves and maintain smooth operations.”
– Joe Ciancimino, CISA, CRISC, cybersecurity expert
The development of ransomware has led to the rise of professional operations that exploit it. These actors use professional offensive-security tools, legitimate administrative and technical support software, malware-as-a-service, and other exploits and malware obtained from the market. There is a convergence around sets of tools, tactics, and practices that no longer belong to specific ransomware operations, espionage, or other motives. These professional groups specialize in gaining access for any willing actor who pays, or multiple actors with different motives.
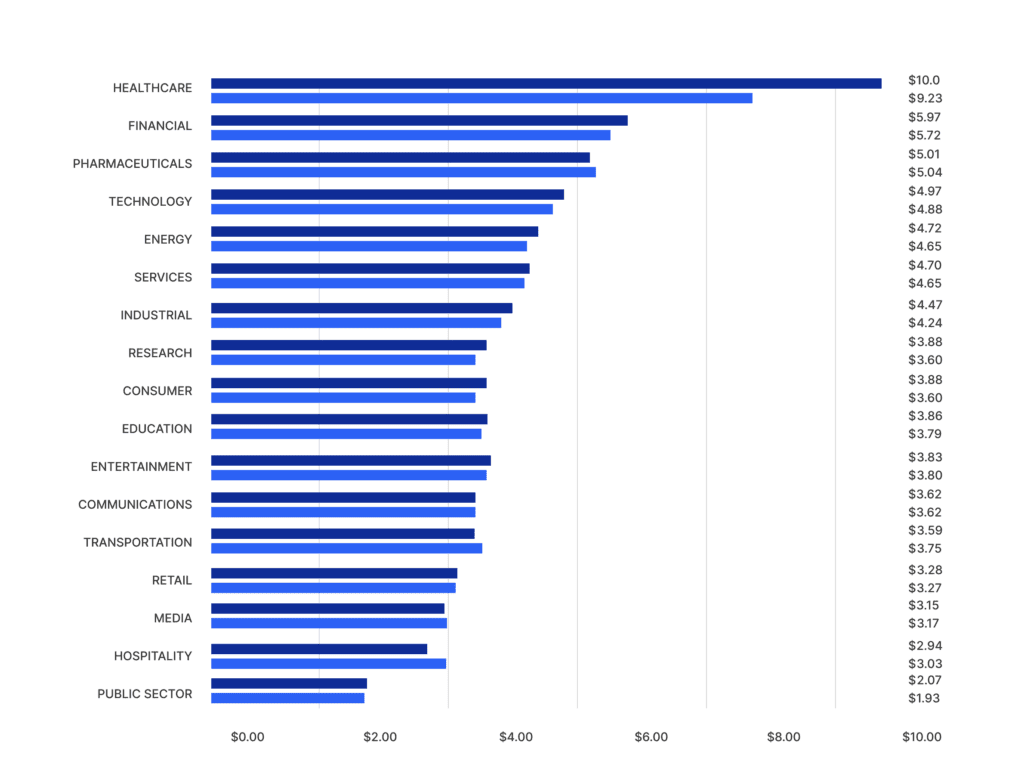
Average Cost of a Data Breach Remediation by Industry
While all industries are targets for ransomware, as shown by the chart below, the average cost of a data breach is highest in the healthcare, financial, pharmaceuticals, technology, and energy industries.
Best Defenses Against a Ransomware Attack
Protecting your business from ransomware is crucial in today’s digital landscape. Here are some steps you can take to enhance your business’s defenses against ransomware attacks:
- Cybersecurity Awareness Training: Train your employees about the risks and best practices for cybersecurity. Teach them about phishing emails, suspicious links in emails, and the importance of strong passwords. Regularly remind them about staying vigilant and reporting any suspicious activities.
- Backup and Recovery: Implement a robust backup strategy for your business data. Regularly back up critical files and systems to an offline or cloud-based backup solution. Ensure the backups are tested periodically to confirm their reliability. In case of a ransomware attack, having a recent backup may enable you to restore your systems without paying ransom.
- Software Updates and Patches: Keep all software, operating systems, and applications up to date. Software updates often contain security patches that address vulnerabilities exploited by ransomware. Enable automatic security updates whenever possible or establish a system to check for security updates manually on a regular basis.
- Strong Passwords and Multifactor Authentication (MFA): Enforce strong password policies for all accounts within your organization. Encourage employees to use complex, unique passwords and avoid reusing them across multiple accounts. Implement multi-factor authentication or two-factor authentication wherever possible to add an extra layer of security.
- Network Segmentation: Segment your network to isolate critical systems and sensitive data from regular user access. This way, even if one segment gets infected, the malware infection will have limited reach, minimizing the damage caused.
- Firewall and Antivirus Software: Deploy a robust firewall to monitor incoming and outgoing network traffic. Combine it with reputable antivirus and anti-malware software to provide an additional layer of protection against known cyber threats.
- Email and Web Filtering: Utilize email and web filtering services to block malicious attachments, links, and websites. These services can help prevent phishing attempts and malicious downloads, reducing the risk of ransomware infections.
- Restrict User Privileges: Implement the principle of least privilege (PoLP), granting employees only the minimum level of access required to perform their tasks. Regularly review and update user permissions based on their roles and responsibilities.
- Incident Response Plan: Develop an incident response plan to handle potential ransomware attacks. The plan should include steps to isolate affected systems, notify relevant stakeholders, involve IT security experts, and restore operations from backups.
- Continuous Monitoring: Implement a comprehensive security measures and monitoring system that includes intrusion detection and real-time threat intelligence. This will enable you to identify and respond promptly to any suspicious activities or attempted breaches.
- Regular Security Audits: Conduct periodic security audits or hire a professional to assess your systems’ vulnerabilities. Regular testing and vulnerability assessments can help identify weaknesses before they are exploited by attackers.
Why Data Backups Are the Best Way to Mitigate Ransomware Attacks
Implementing a secure backup schedule is crucial in reducing expenses and restoring operations after a ransomware attack. Furthermore, it provides additional protection from potential disruptions such as system outages, natural disasters, hardware failure, software corruption, human error, theft and loss of devices.
It cannot be guaranteed that paying the ransom will result in data decryption or return by ransomware actors. However, organizations that utilize backups for data recovery experience faster recovery times compared to other methods, as described below.
How Often Should Your Company Backup Data?
The frequency of data backup for your company should be determined based on factors such as business size, data generation rate, industry, and recovery requirements. Generally, a full backup should be conducted weekly or monthly to serve as a baseline for incremental or differential backups. Incremental backups, which only save data changes from the last incremental backup, can be done daily or even more frequently, depending on your company’s needs. Differential backups, on the other hand, store data changes since the last full backup, and can be performed daily or every few days, based on the critical nature of the data.
For businesses handling highly critical data or experiencing frequent data changes, real-time or continuous backup solutions might be appropriate, as they back up data immediately or at very short intervals. It’s essential to assess your company’s specific needs, risk tolerance, and regulatory requirements to determine the most suitable backup frequency. Incorporating an offsite or cloud-based backup in your strategy is also recommended to ensure data protection and accessibility in the event of local disasters or hardware failures.
Related article: How Often Should Your Business Backup Its Data?
RTO and RPO: What They Are and Why They Matter
Before determining the frequency of a business’s data backup, it’s important to understand the concepts of RPO and RTO. Ideally, a backup strategy should be in place that allows for immediate restoration after a ransomware attack or disaster, with systems fully restored as quickly and seamlessly as possible. RTO and RPO are big, big parts of how you get to that point.
- RTO (recovery time objective) refers to the total amount of time that an application or a critical system can be down without causing some level of significant damage to your business. Meaning, of course, that this is the minimum amount of time that can go by before you start to accrue costs due to downtime, lost productivity or similar issues.
- RPO (recovery point objective), on the other hand, directly relates to your company’s overall data loss tolerance. To put it another way, this is the maximum amount of data that you can realistically lose before significant harm occurs.
Calculating Backup Frequency with RTO & RPO
It’s essential to understand that there is no single solution or perfect number when setting RTO and RPO for businesses facing the risk of ransomware or other disruptive events. Each business is different, so determining the acceptable level of loss before reaching the “point of no return” is crucial.
The frequency of backing up business data is influenced by factors like secure location and time intervals. Examining internal metrics is essential for determining RPO, while RTO requires evaluating the downtime your business can afford before it’s severely impacted.
In a nutshell, businesses should assess their tolerance for data loss to determine their RPO and RTO. For instance, if losing four hours’ worth of data is unacceptable, set your RPO at four hours and back up systems accordingly. Remember, downtime isn’t just about data recovery; it also impacts productivity and revenue. So, allocate resources smartly to meet both RPO and RTO objectives.
Recovering Critical Applications and Data
In the event of a ransomware attack or a sudden business disruption, prioritize getting critical applications up and running as soon as possible, while addressing non-critical applications later. Time management is key in this situation. RTO focuses on the time limit for application downtime before things become problematic, while RPO is concerned with the amount of data you can lose before your business is negatively impacted.
Optimizing Backup and Disaster Recovery Strategy
Real-time replication to a hotsite is the best solution for disaster recovery. Back up critical data as often as possible to prepare for cyberattacks and disasters. However, it may not always be economically feasible for all organizations. Defining RTO and RPO metrics is crucial for an effective backup and disaster recovery strategy, as it allows you to assess known threats and risks. This approach ensures that you have done everything possible to remain protected given the circumstances.
Therefore, these two related-yet-different concepts are very much two sides of the same coin. They’re the metrics at the heart of your backup and disaster recovery plans and, once you’ve taken the time to define the appropriate parameters for your business, you will have a roadmap to exactly how often you should be backing up your data.
Related article: Steps to Identify the Most Critical Data for Your Business.
OuterEdge | Data Backups & Security Best Practices 24/7
If you’d like to find out more about how to fortify your systems and data against ransomware attacks including how disaster recovery and backup solutions fit into that defense and align with your RPO/RTO requirements – the expert service provers at Outer Edge are here to help. Give us a call at 844-OET-EDGE or fill out the form on our website to schedule a meeting today.
Frequently Asked Questions about Ransomware
Resources
- IBM. (2022). “Cost of a data breach 2022: A million-dollar race to detect and respond.” Retrieved from https://www.ibm.com/reports/data-breach.
- Stouffer, Clare. Norton (2021). “Types of Ransomware. Retrieved from https://us.norton.com/blog/malware/types-of-ransomware.
- Verizon. (2022). “Data Breach Investigations Report.” Retrieved from https://www.verizon.com/business/resources/reports/dbir/.
- Sophos. (2023). “The State of Ransomware 2023.” Retrieved from https://www.sophos.com/en-us/content/state-of-ransomware.
- AWA Infosec. (2022). “The Hidden Costs of Ransomware.” Retrieved from https://awainfosec.com/blog/hidden-costs-ransomware/







